Adenia Partners (“Adenia”), a leading private equity firm focused on growth opportunities in Africa, has successfully closed its fifth fund, Adenia Capital V (the “Fund”, “AC(V)” or “Fund V”) at its $470 million hard cap. The Fund, which was significantly oversubscribed, attracted commitments from new and existing investors globally.
As organisations step up efforts to leverage the capabilities of artificial intelligence (AI), it is essential for both AI developers and regulators to consistently contemplate, integrate, and advocate for ethical considerations throughout the entire process. That’s according to Hope Lukoto, Chief Human Resource Officer at BCX, who points out that while AI promises a plethora of business benefits, responsible use of the technology is key to unlocking its full potential.
The Jennifer Ward Oppenheimer Research Grant (JWO Grant) was established in 2019 to honour the legacy of the late.
We are witnessing a clash between businesses pushing for in-office work and Gen Z workers who prioritise flexibility, environmental consciousness, and inclusivity. Even remote-working advocate, Zoom, has demanded that those within 80km of the office need to work in-person twice a week. As Gen Z becomes the dominant demographic in the future workforce, project-based independent contracting and remote collaboration are gaining popularity as preferred modes of work. Gary Silbermann, Co-Founder & Innovation Director at One Degree shares that there doesn’t have to be an ongoing battle between C-suites and younger workers.
Kenya faces the formidable challenge of aligning its climate action with its development goals.
The African Continental Free Trade Area (AfCFTA) is predicted to increase Africa’s trade income by USD 450 billion by 2035 and will boost intra-African trade by more than 81 percent, according to a recent report by the World Bank.
Africa’s mid-market businesses, the backbone of the continent’s economic growth, can find themselves trapped in a financing void. With annual revenues typically surpassing $10 million, these companies find themselves in a precarious position – too large for microfinance, yet too small or risky for traditional banks.
Hilton’s lifestyle brand Curio Collection by Hilton debuts in Kenya, with a fusion of historic charm and a refined contemporary design for an immersive guest experience.
In an era where change is the only constant, businesses must adapt and evolve to stay ahead. Penquin, the brand and communication agency based in Johannesburg, is leading by example, embracing transformation with open arms. The agency recently made headlines with the unveiling of its brand-new logo and refreshed corporate identity (CI), marking a significant milestone in its journey.
As Africa’s travel and tourism industry surges, fueled by a growing middle class and a projected CAGR of 8.9% or $731.4 billion by 2032 in the “bleisure” market, the demand for innovative hospitality solutions is booming.
In 2024, Egypt and the Big 5 global hotel chains—Accor, Hilton, IHG, Marriott International, and Radisson Hotel Group—lead Africa’s hotel development, capturing a market share of 28% and 71% respectively, as per the latest African Hotel Chain Development Pipeline report by W Hospitality Group. With over 92,000 rooms in 524 hotels across the continent, the report highlights a surge in resort growth and Egypt’s remarkable dominance in the market.
According to NIQ, 44% of South African consumers feel they are in a worse financial position this year compared to a year ago. Of those respondents, 82% say that increased costs of living are to blame for their recent financial struggles, up from 76% a year ago. Nearly two-thirds (62%) state they are worse off due to the economic slowdown, up from 57% a year ago. These findings appeared in “Consumer Outlook 2024″, the latest NIQ Thought Leadership report capturing the mindset and sentiment of consumers around the world.
The Africa Fintech Summit (AFTS) releases its insightful “Nigeria Fintech Marketing Outlook 2024” report, shedding light on the current state and future direction of marketing strategies within the nation’s booming fintech industry.
In the article, Rodney Taylor, MD at Guardian Eye, sheds light on the multiple challenges faced by healthcare systems in Africa, such as accessibility, cost constraints, and the potential for digital technologies to transform the sector. He argues that technology can only be effective if it is accessible, affordable, and culturally appropriate.
The use of blockchain practices has been rising in every industry. Today, every single industry is making the most out of it and making things easier for their audience to deal with it. If you are thinking how blockchain practices is going to get better with digital transformation, then you have landed on the right page.
In this essential guide for homeowners, we explore in depth the strategies and preventive measures crucial to effectively protecting your home from termites.
Enabling African Innovators to Get Seen, Get Connected, and Get Funded
Fintechs are driving financial inclusion in sub-Saharan Africa by providing safer and more affordable solutions for cross-border remittances, reducing costs by 50% in the past decade. These fintechs are enabling people to join the formal economy and access a range of financial services, contributing to lasting financial inclusion in the region.
Morocco is fast becoming a sought-after destination on the continent. This diverse country, with its blend of ancient traditions and modern allure, offers travellers distinct experiences in its major cities, making it immensely popular. From diverse landscapes and desert adventures to vibrant souks, hammams and historical sights, Morocco has it all.
According to the World Health Organization, the sale of counterfeit medication is the world’s most lucrative illicit trade. Sadly, Africa has become home to an estimated 42% of the world’s cases of trade in counterfeit medications, disproportionately affecting the most vulnerable and desperate of populations living in low- or middle-income countries.
This piece discusses the critical shift from omnichannel to ambient technology and the need for retailers to ground their aspirations in reality.
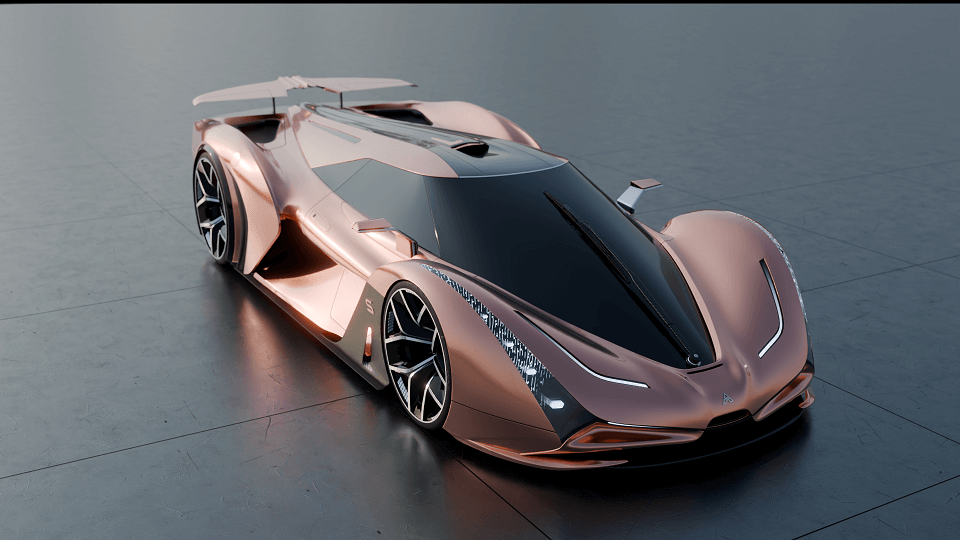
The Ararkis Sandstorm, a rare edition electric Hypercar with South African roots, blew through an online cloud of controversy last week when the internet erupted over the ‘tailpipes’ found on the car’s rear end.